Secure Your Network with Zero Trust Network Access (ZTNA)
What is ZTNA in Cybersecurity
and how does it work?
ZTNA 1.0 vs ZTNA 2.0
ZTNA 1.0
Basic authentication methods
Limited application support
Limited cloud integration
Basic security controls
Moderate user experience
ZTNA 2.0
Enhanced authentication options
Broader application support
Improved cloud integration
Advanced security controls
Improved user experience
Advanced Access Control Solutions for Total Security
Zero Trust Access Control
Network Access Control (NAC)
Service-Based Access Control
User-Managed Access (UMA)
Group-Based Access Control
Gateway/Location-Based Control
Identity-Based Access Control (IBAC)
Policy-Based Access Control (PBAC)
Attribute-Based Access Control (ABAC)
Device Posture Check
Why Is ZTNA Better Than Traditional
VPN for Secure Access?
hardware and is managed via a unified console for easy operation.
modern, distributed work environments.
What Are the Key Differences Between
ZTNA and SASE?
- ZTNA
- SASE
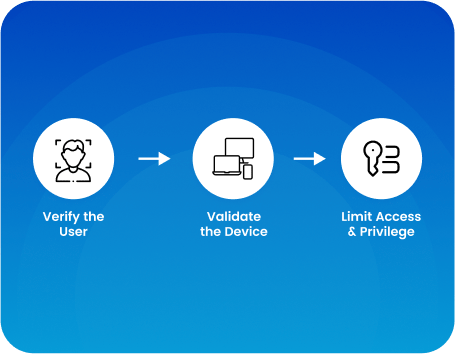
Key Features of ZTNA
- Focuses solely on secure remote access without built-in networking capabilities.
- Restricts access to specific, pre-defined services for authenticated users.
- Designed for targeted applications and services for remote users.
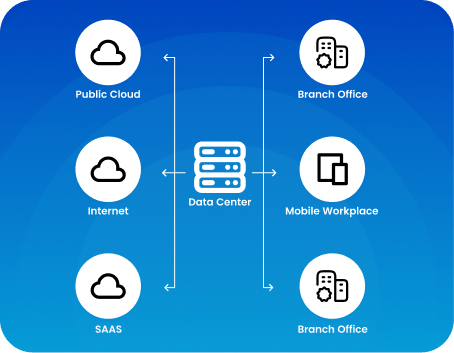
Key Features of SASE
- Combines networking and security into a cloud-based service for remote and hybrid users.
- Leverages cloud-based capabilities with flexible deployment.
- Simplifies operations by consolidating multiple functions into one solution.
Why Combine ZTNA and SASE for
Modern Cybersecurity?
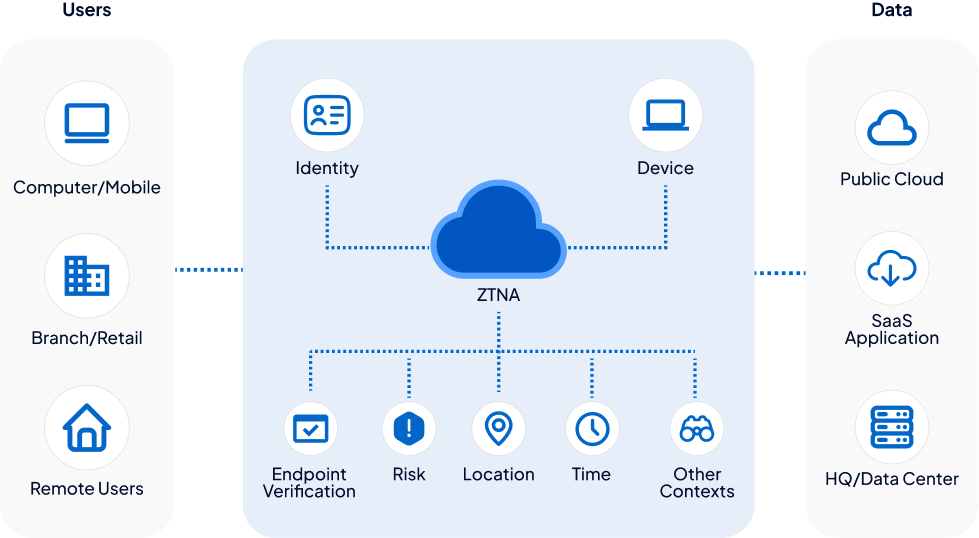
Zero trust network access technology Use Cases
Redefining secure access with least privilege and adaptive authentication for modern enterprises.
(IAM) & SaaS Security
Strengthens identity management with centralized authentication, SSO, and secures SaaS apps.
Secure Remote Access and VPN Alternative
Offers precise controls for hybrid work, replacing VPNs, and safeguarding internal resources.
Third-Party & DevOps Security
Grants limited access to third-party vendors and ensures authorized personnel access in DevOps.
Healthcare Data Security
Supports regulatory compliance with multifactor authentication and protects encrypted patient records.
Global Collaboration & Education Security
Provides secure virtual workspaces for global teams and protects sensitive educational data.
Comprehensive Enterprise Security Framework
ZTNA is a complete security solution, securing remote access, SaaS apps.
Discover the Best ZTNA Solutions
Who Are the Top ZTNA Providers for Secure Access?
Why Is Pure Dome a Leading ZTNA Provider?
Read our Customer Stories
See What Our Partners Are Saying
One of the best VPN that I usedIt gives me a lot of location to use, and the best part is, chat support is just a second a way. The response was fast and the chat support is great. I appreciate the help with Adam who did solve my problem right away.
PureDome is easy to use from the Admin side and user side. It was easy to implement. Customer support helped all the way whenever needed. Frequency of use on a daily basis Easy integration with Google Chrome.
Easy to use and Best support, PureDome is a reliable ZTNA provider. We use it as we travel a lot and we need to access to company resources, having many great features like Dedicated IP and Gateways! and it is very easy to implement as well.
It works well, despite the constant VPN blocking by Roskomnazdor.If connection difficulties arise, technical support promptly helps resolve the issue.
Educational Resources
Frequently asked questions
What is ZTNA in cybersecurity?
ZTNA (Zero Trust Network Access) is a security model that provides controlled access to resources by verifying user identity and device posture, applying the "never trust, always verify" principle.
Does ZTNA have MFA authentication?
Yes, ZTNA incorporates Multi-Factor Authentication (MFA) to strengthen identity verification and enhance security.
What’s the difference between ZTNA and SASE?
ZTNA secures access to individual resources, while SASE combines ZTNA with SD-WAN and other security solutions to deliver secure, holistic network access.



