Device Posture Check: Operationalize Zero Trust with Puredome
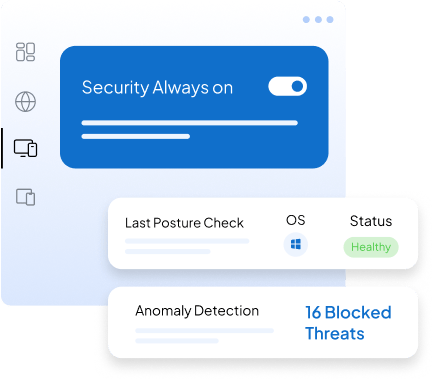
What is Device Posture Check?

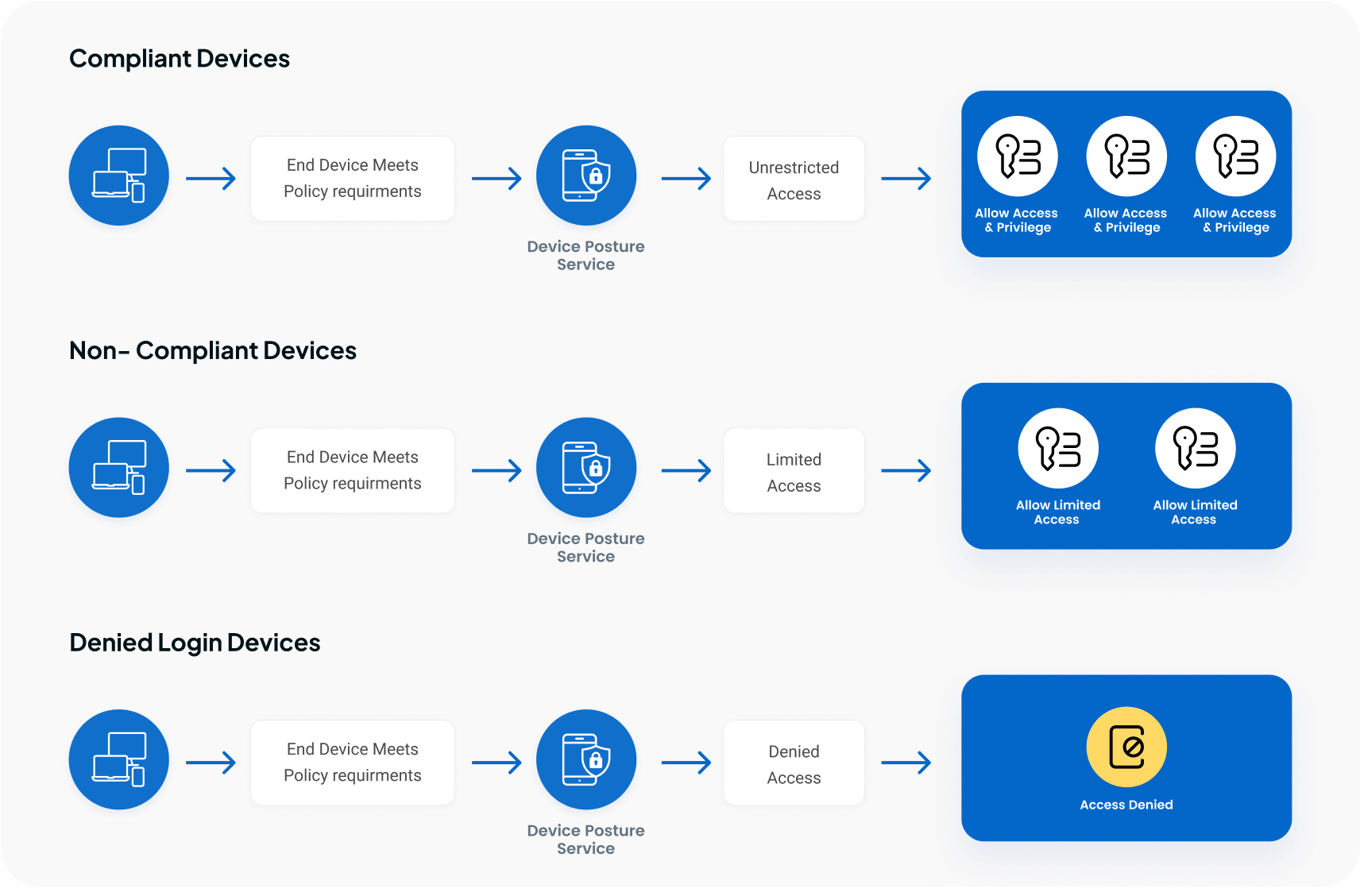
How Device Posture Check Works?
Key Features of Device Posture Check
Centralized Enforcement and Compliance
Identify devices that are unfamiliar or compromised (e.g., jailbroken/rooted) to prevent potential risks.
Detection of Unknown or Rooted Devices
Monitor devices to ensure they are using authorized OS versions and have the latest software updates for security.
Ensuring OS and App Updates
Alert administrators when devices fail to meet security standards and prevent their access to the network.
Notify and Block Non-Compliant Devices
Review past compliance states and generate detailed reports for security audits and analysis.
Auditing and Analyzing Historical Data
Limit or allow network access based on the geographical location of devices, enhancing security.
Location-Based Network Access Control
Alert administrators when devices fail to meet security standards and prevent their access to the network.
Why Device Posture Check is Important
Device Posture Check Overview

Manage Profiles Effortlessly
- Maximum 3 profiles per account
- Tailored for secure and flexible management
across teams and devices
Supported Operating Systems
- Mac
- Windows
- iOS
- Android
- Linux


Scheduling Frequency
- Prior to connection
- Every 20 minutes
- Every 40 minutes
- Every 60 minutes
Supported Rules
- Antivirus verification
- Certificate authentication
- Operating system version compliance
- Disk encryption enforcement
- Torrenting block
- File existence checks
- Process monitoring
- Registry integrity
- Windows Security Center
- Active Directory
- Rooted device detection

Device Posture Check Overview
Trusted by companies of all shapes and sizes
See What Our Partners Are Saying
One of the best VPN that I usedIt gives me a lot of location to use, and the best part is, chat support is just a second a way. The response was fast and the chat support is great. I appreciate the help with Adam who did solve my problem right away.
PureDome is easy to use from the Admin side and user side. It was easy to implement. Customer support helped all the way whenever needed. Frequency of use on a daily basis Easy integration with Google Chrome.
Easy to use and Best support, PureDome is a reliable ZTNA provider. We use it as we travel a lot and we need to access to company resources, having many great features like Dedicated IP and Gateways! and it is very easy to implement as well.
It works well, despite the constant VPN blocking by Roskomnazdor.If connection difficulties arise, technical support promptly helps resolve the issue.
Your best cybersecurity
experience awaits.
Get 5 individual VPN accounts at the lowest price ever.



