- Product
-
Solution
-
By Industry
Cybersecurity solutions tailored to your industry’s needs.
-
- Resources
-
Books
Our ultimate guides and playbooks
Solution Briefs
Overview of PureDome’s functionality
-
Quizzes
Assess your cybersecurity readiness
Case Studies
PureDome customer success stories
Newsletter
Subscribe to the PureDome newsletter
-
- About Us
- Partner
- Pricing
- Download
Managing Protected Health Information (PHI) in Compliance with Global Regulatory Frameworks
-
Sharmeen Saleem
-
30 Jan 2024
- 6 min read
%20in%20Compliance%20with%20Global%20Regulatory%20Frameworks.webp)

If you're considering HIPAA compliance or exploring partnerships with healthcare organizations, you've probably heard of PHI—Protected Health Information. It's a key part of HIPAA regulations meant to enhance the security of patients' private data.
Ensuring HIPAA compliance is crucial for organizations working in or partnering with the healthcare industry. Safeguarding a patient’s medical records and personal information goes beyond avoiding penalties—it's vital for building trust with you, the patients, and, in the end, delivering exceptional patient care.
Here's what you and your partners in health organizations need to know about managing PHI in compliance with the global regulatory frameworks.
Compliance Challenges in Telehealth
In an era where healthcare data is experiencing exponential growth and digital technology is omnipresent, you may find yourself navigating the increasing complexity and significance of managing protected health information (PHI). For instance, as of 2017, a single patient could generate nearly 80 megabytes of imaging and EMR data annually. Between 2009 and 2021, around 95% of the US population had their medical information disclosed, highlighting the vulnerability of healthcare data. Additionally, employees in healthcare organizations have access to nearly 20% of files, which can increase the risk of data exposure.
Projections indicate that the compound annual growth rate for healthcare data could reach 36% by 2025, surpassing many other industries. The COVID-19 pandemic further intensified data generation, making previous estimates conservative. However, despite this surge, the healthcare sector lags in IT investment, presenting a challenge to managing this influx effectively.
With the rise of telemedicine, wearable health devices, and the adoption of electronic health records (EHRs), the volume of PHI being generated and shared is increasing significantly. This influx of data necessitates a proactive approach to regulation, focusing on security and privacy concerns.
What is Protected Health Information (PHI)?
Protected Health Information, or PHI, is a term established within the Health Insurance Portability and Accountability Act of 1996 (HIPAA) framework. HIPAA, a federal law, was enacted to develop nationwide standards to safeguard sensitive patient information, preventing unauthorized disclosure without consent.
PHI encompasses any health-related data generated, transmitted, or stored by a HIPAA-covered entity. This inclusive scope comprises electronic records (ePHI), written documentation, lab results, x-rays, bills, and verbal conversations containing personally identifying information.
Delving deeper into the definition of PHI is crucial for organizations to assess whether they collect such data and implement effective protection measures.
Comparison of Global Compliance Regulations
To effectively manage PHI compliance, the covered entities must navigate a range of global data privacy regulations.
Here is a comparison table to help you understand the four most influential regulations:
| Regulation | Description | Notification Timeline & Penalties |
|---|---|---|
| HIPAA (United States) | Healthcare data regulation in the United States. | 60 days Up to $1.5 million |
| GDPR (European Union) | General Data Protection Regulation in the European Union. | 72 hours Up to €20 million |
| CPIPEDA (Canada) | Personal Information Protection and Electronic Documents Act in Canada. | 30 days Up to $100,000 |
| HITECH Act (United States) | Health Information Technology for Economic and Clinical Health Act in the United States. | 60 days Up to $1.5 million |
How Can You Secure PHI?
HIPAA compliance necessitates organizations to implement measures to ensure the protection of PHI from unauthorized access. However, the specific actions covered entities must take are not explicitly listed in HIPAA rules. This flexibility allows organizations to determine the most suitable security measures based on size and function. For instance, a regional hospital system might have different requirements and controls compared to a small family clinic.
As a covered entity, it's your responsibility to implement safeguards against PHI breaches. The HIPAA Security Rule outlines various administrative, physical, and technical safeguards for you to consider. These may involve creating access management policies, providing employee training, establishing incident response plans, implementing document shredding practices, and incorporating data encryption measures.
PHI Compliance: Global Healthcare Data Requirements
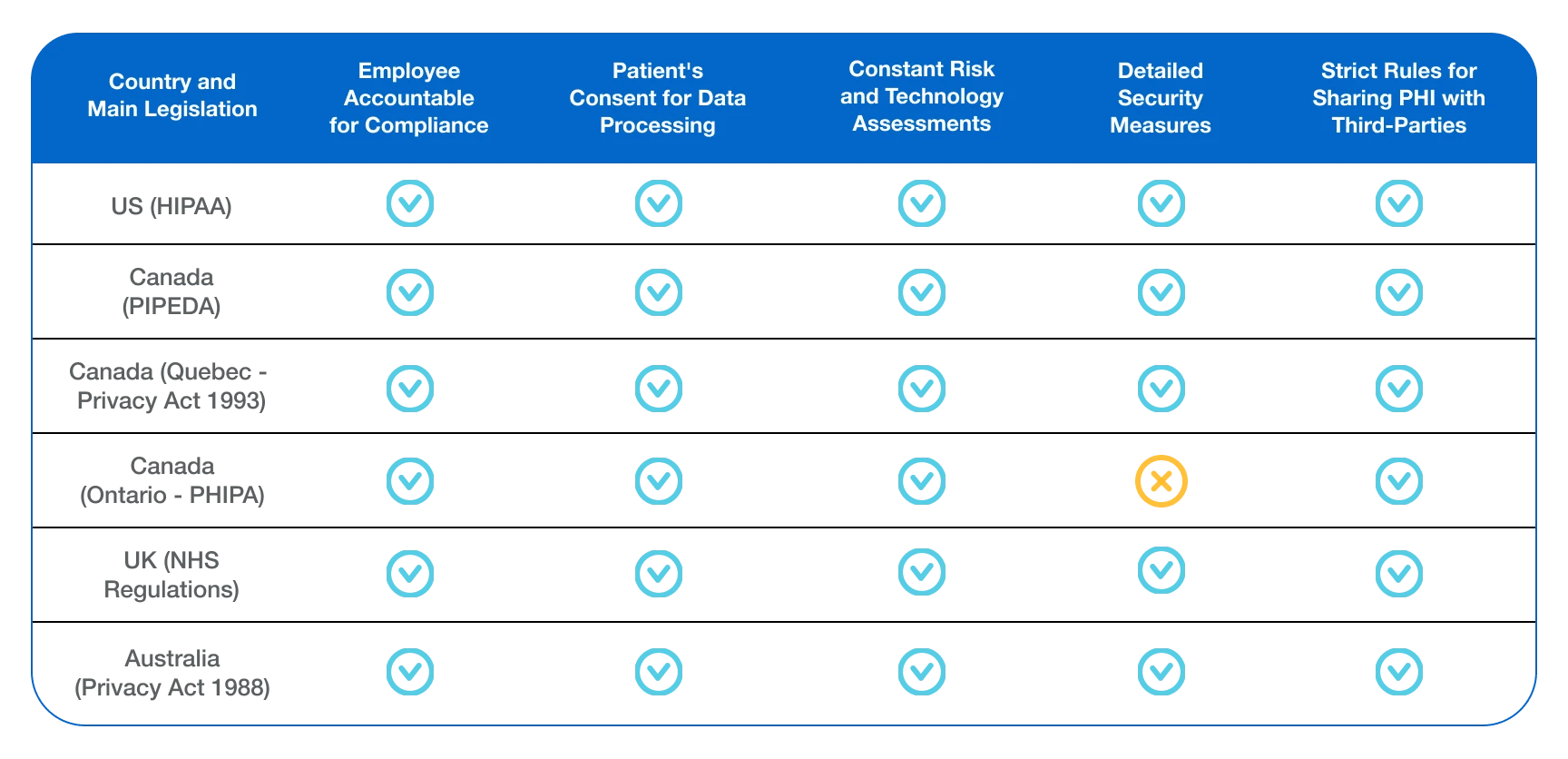
Meeting HIPAA Regulations: Are you in Compliance?

Meeting HIPAA standards is an ongoing challenge—and if you don’t have the right processes in place, it can be challenging to keep up with. For medical facilities like yours that hire virtual aim to stay compliant, it begins with the following best practices:
Annual Employee Training
Alongside employee training, it's crucial to embed access controls and ensure maximum security to minimize the risk of data breaches. Using compliance technology software, your company can also enhance the security of its facilities and devices.
Enhance Security Measures
Alongside employee training, it's crucial to embed access controls and ensure maximum security to minimize the risk of data breaches. Using compliance technology software, your company can also enhance the security of its facilities and devices.
Thorough Documentation for Compliance
Every policy and process created to protect PHI should be thoroughly documented in your company for at least six years. This documentation includes records of all privacy policies, complaints, remediation plans, and other relevant documentation.
Conduct Risk Assessments and Audits
Your team should regularly conduct risk assessments and internal audits. To achieve this, set up risk assessments for unauthorized file transfers, account logins, or access/modification of data, controls, or configurations.
HIPAA Violations: Consequences for Unauthorized Disclosure of PHI
Failure to safeguard Protected Health Information (PHI) in accordance with HIPAA rules may result in fines by the Department of Health and Human Services Office for Civil Rights. Violations carry substantial costs, extending beyond monetary penalties to potentially causing lasting harm to your organization's reputation and undermining patient trust.
Here are several common PHI violations that should be avoided:
Sale of PHI
Covered entities are prohibited from selling PHI without proper authorization from the patient. Organizations found knowingly disclosing or selling PHI without authorization may face a HIPAA violation fine of up to $50,000 and one-year imprisonment.
Mismanagement of Access to PHI
It is imperative to limit access to PHI for payment, treatment, or healthcare operations. Any shared access to PHI must have explicit authorization from the patient. Additionally, you must ensure that PHI is permanently and securely destroyed when it is no longer necessary. Managing access to PHI also involves responding promptly to a patient's request for their medical records.
Breach Notification Rule
As a covered entity, you must notify affected individuals within 60 days of a breach involving unsecured PHI. Failure to do so constitutes a violation of the HIPAA Breach Notification Rule.
Minimum Necessary Rule
Despite often requesting access to a patient's complete medical history, as a healthcare provider, you may also seek specific PHI. The Minimum Necessary Rule stipulates that covered entities should only disclose PHI directly relevant to the request. In any case, PHI can only be disclosed to a third party with explicit patient authorization unless it is directly linked to healthcare treatment, operations, or payment.
Case Example: Anthem Inc.'s Non-Compliance with PHI Regulations

Anthem is a health insurance provider that extends medical care coverage to approximately one in eight Americans through its affiliated health plans. The security breach in question impacted the electronic protected health information (ePHI) maintained by Anthem, Inc. for its affiliated health plans.
Incident Overview:
In 2015, Anthem Inc. fell victim to a cyber-attack where malicious actors successfully breached the organization's systems. Anthem reported a breach to the HHS Office for Civil Rights, revealing that cyber-attackers had gained access to their IT system. Subsequent investigations disclosed that the attackers had infiltrated the system through spear phishing emails sent to an Anthem subsidiary. At least one employee responded to the malicious email, unwittingly facilitating further cyber-attacks. This breach resulted in the unauthorized access and theft of electronic PHI belonging to approximately 78.8 million individuals.
Consequences of Non-Compliance:
Anthem Inc. was fined $16 million by the Department of Health and Human Services (HHS) for PHI non-compliance after a security breach, contributing to a total financial impact of $48.2 million, inclusive of fines and settlements from related lawsuits.
Lessons Learned:
Anthem Inc.'s case is a stark example of the potential consequences of inadequate PHI protection. It underscores the importance of compliance with regulations and robust security measures to safeguard patient information and mitigate the reputational and financial risks associated with non-compliance.
Compliance and Data Sovereignty Hurdles
If you have remote staffing needs, then securing remote access becomes even more crucial, emphasizing the necessity to align these practices with HIPAA compliance standards.
One of the key challenges in PHI compliance is providing secure remote access to healthcare professionals while maintaining compliance. Business Virtual Private Networks (VPNs) offer a tangible solution. By encrypting data transmitted between remote locations and central servers, business VPNs ensure the confidentiality and integrity of PHI. Moreover, they allow for granular control over access rights and can log and audit remote connections, aiding in compliance with regulatory audit procedures.
Large international healthcare companies often grapple with compliance complexities due to varying regulations across jurisdictions and data sovereignty hurdles. Here are actionable strategies to address these challenges:
- Centralized Data Management: Implement a centralized data management system that adheres to the strictest regulations among the jurisdictions in which the company operates. This ensures a consistent standard of PHI protection.
- Consult Legal Experts: Seek legal expertise to navigate the complex landscape of international data privacy laws. Engaging local legal counsel can help ensure compliance while respecting data sovereignty requirements.
- Data Localization: Where necessary, consider data localization practices to keep PHI within specific jurisdictions, mitigating data sovereignty concerns.
Conclusion
As you aim to enhance the overall customer experience in your healthcare facility, it is crucial to adhere to HIPAA privacy and security regulations. Safeguarding Protected Health Information (PHI) becomes a pivotal aspect of your efforts. An effective strategy for achieving PHI compliance involves protecting data at rest, in motion, and during use. This includes implementing robust, encrypted backups to prevent the loss of stored patient information, adopting multifactor authentication to restrict data access to authorized users, and utilizing a HIPAA-compliant VPN solution to secure data in transit.
Stay up to date with the latest cybersecurity insights and best practices
Get the latest information, stories, and resources in your inbox. Subscribe for monthly updates.
Securing 1000+ Businesses Across The World