- Product
-
Solution
-
By Industry
Cybersecurity solutions tailored to your industry’s needs.
-
- Resources
-
Books
Our ultimate guides and playbooks
Solution Briefs
Overview of PureDome’s functionality
-
Quizzes
Assess your cybersecurity readiness
Case Studies
PureDome customer success stories
Newsletter
Subscribe to the PureDome newsletter
-
- About Us
- Partner
- Pricing
- Download
Why IT Solutions for Healthcare Must Prioritize Secure Remote Access
-
Aiman Ikram
-
24 Mar 2025
- 3 min read

Did you know that almost 89% of healthcare organizations have experienced a data breach in the past year. That’s almost nine out of ten. In an industry where protecting patient data is a legal and ethical obligation, that number should be alarming for every IT manager.
Now, add remote work into the mix—telehealth, remote billing, cloud-based records—and the risks multiply. Every unsecured connection is a door left ajar for cybercriminals. So, how do healthcare IT teams keep everything locked down while still making remote access seamless?
The Risks Are Bigger Than You Think
Cybersecurity threats aren’t just about stolen passwords anymore. They’re far more sophisticated and relentless with each passing day. And what is worse is that they are specifically targeting healthcare. Why?
- Healthcare data is worth more than credit card info – A single patient record can sell for up to $1,000 on the dark web. Compare that to just a few bucks for a stolen credit card.
- Ransomware attacks are skyrocketing – The healthcare sector saw a 94% increase in ransomware attacks in 2023 alone. Hospitals have even been forced to shut down operations.
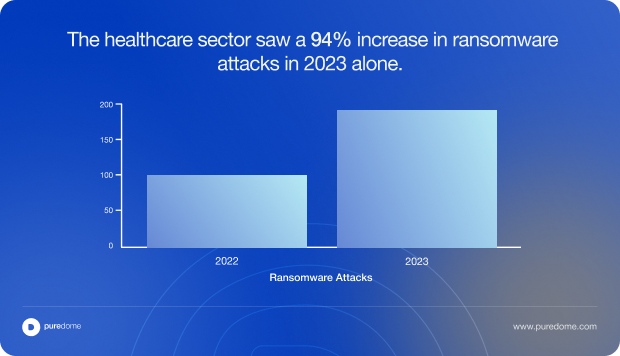
- Regulatory fines are steep – Non-compliance with HIPAA can mean fines up to $1.5 million per violation per year. And that’s not counting lawsuits or reputational damage.
This means that security isn’t optional. It’s survival.
Remote Work Is Here to Stay—So Are the Security Gaps
Remote access isn’t just about letting employees log in from home. It’s now an essential part of patient care, medical research, and billing operations. But as hospitals and clinics embrace remote work, many haven’t fully addressed security gaps.
- Telehealth adoption increased by 38x since 2020, but many platforms still rely on basic authentication methods.
- Remote medical billing teams are accessing patient records from various locations, increasing exposure to phishing and credential theft.
- Contract healthcare workers often use personal devices to log into hospital systems, creating weak entry points.
Without a strong remote access strategy, healthcare organizations are left vulnerable.
Why Traditional VPNs Don’t Cut It
Despite the increasing cyberthreats, a lot of healthcare teams still rely on traditional VPNs for their network security. They think, “Well, it encrypts data, so we’re good, right?” Not quite.
- They’re not built for scale – Legacy VPNs struggle with multiple remote users, leading to slow speeds and connection drops.
- They create a single point of failure – If one user’s credentials are compromised, the entire network could be at risk.
- Lack of granular access control – Most traditional VPNs don’t let you set user-specific permissions, meaning a billing employee could access the same sensitive data as a senior physician.
- They don’t integrate with modern security frameworks – Zero Trust and identity-based access control are essential, but most legacy VPNs don’t support them.
This isn’t about just adding another security layer. It’s about rethinking how remote access should work in a world where threats evolve daily.
What Secure Remote Access Needs to Look Like
Before we move on to discussing the solutions, let’s break down what actually makes remote access secure in terms of healthcare. To be truly secure, a remote access solution should:
- Use Zero Trust principles – No one gets in without verification, even if they’re already inside the network.
- Enable role-based access control (RBAC) – A nurse should not have the same data access as a hospital administrator.
- Encrypt data end-to-end – Not just on the device, but across every point of transmission.
- Offer seamless integration – Security is useless if employees find workarounds because it’s too complicated.
- Provide dedicated network access – Keeping internal systems separate from public internet connections reduces risk.
- Monitor for threats in real-time – Anomalous access attempts need to be flagged and acted upon immediately.
The Hidden Costs of Insecure Remote Access
A security breach doesn’t just put data at risk—it disrupts entire healthcare operations. From delayed treatments to regulatory scrutiny, the fallout can be severe if not taken seriously.
- Downtime from cyberattacks – A single ransomware attack can shut down a hospital for an average of 15 days.
- Loss of patient trust – A survey found that 75% of patients would consider switching providers if they felt their data wasn’t secure.
- Operational inefficiencies – Slow or unreliable remote access means wasted time for medical professionals, impacting patient care.
The Solution: Secure Remote Access With PureDome

This is where PureDome comes in. Trusted by over 3000 users, it is built for teams that need secure, scalable remote access—without the hassles of traditional VPNs and security tools. With PureDome, healthcare IT teams can:
- Assign dedicated IPs for secure, compliant access to patient data.
- Enforce Zero Trust principles without complicating workflows.
- Ensure end-to-end encryption for every remote connection.
- Scale seamlessly as telehealth and remote teams expand.
- Monitor network activity in real-time for better security oversight.
Healthcare security is too high-stakes for outdated solutions. The right remote access approach isn’t just about compliance—it’s about protecting patient trust, avoiding catastrophic breaches, and keeping critical systems running. Get started with PureDome here.