- Product
-
Solution
-
By Industry
Cybersecurity solutions tailored to your industry’s needs.
-
- Resources
-
Books
Our ultimate guides and playbooks
Solution Briefs
Overview of PureDome’s functionality
-
Quizzes
Assess your cybersecurity readiness
Case Studies
PureDome customer success stories
Newsletter
Subscribe to the PureDome newsletter
-
- About Us
- Partner
- Pricing
- Download
How to Prevent Data Breaches in 2024
-
Aiman Ikram
-
25 Jun 2024
- 3 min read

In today's digital age, a data breach can cripple your business overnight. Are you prepared to fight back and protect your valuable information? This blog helps you learn the top strategies to prevent data breaches in 2024 and keep your data secure.
What Is A Data Breach?
A data breach is when unauthorized individuals gain access to confidential information without permission. This can involve personal data, financial records, or any sensitive information. Imagine someone breaking into your home and stealing valuable items—except in a data breach, it's your digital information that's at risk. Understanding what a data breach is and how it happens is the first step in protecting your data from cybercriminals.
2024 Key Insights
- 45% of Americans have had their personal information compromised by a data breach in the last five years.
- 82% of data breaches involve data stored in the cloud, with 39% of breaches spanning multiple environments and incurring an average cost of $4.75 million.
- 86% of data breaches involve the use of stolen credentials.

How Does a Data Breach Happen?
Weak Passwords: If passwords are simple or reused across different accounts, hackers can easily guess or use tools to crack them, gaining access to sensitive information.
Phishing Attacks: Cybercriminals send deceptive emails or messages that trick people into providing personal information or clicking on malicious links, which then grant the hackers access to their data.
Unpatched Software: When software isn't updated regularly, it can have security vulnerabilities. Hackers exploit these weaknesses to infiltrate systems and steal data.
Malware: Malicious software, like viruses or spyware, can be unknowingly downloaded and installed on devices, allowing hackers to access and steal information.
Insider Threats: Sometimes, employees or others with access to sensitive information may intentionally or accidentally leak data, leading to a breach.
Unsecured Networks: Using public Wi-Fi or unsecured networks can expose data to hackers who are monitoring these networks, making it easy for them to intercept and steal information.
Data Breach Prevention Strategies for 2024
Strong Password Policies: Use complex passwords that include a mix of letters, numbers, and symbols. Change passwords regularly and avoid using the same password for multiple accounts. Encourage the use of password managers to securely store and manage passwords.
Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security by requiring two or more verification methods. Common methods include text message codes, authentication apps, or biometric scans. This ensures that even if a password is compromised, unauthorized access is prevented.
Regular Software Updates: Keep all software, operating systems, and applications up to date with the latest security patches. Enable automatic updates where possible to ensure timely installation of critical fixes. Regularly review and update security settings on all devices.
Employee Training and Awareness: Conduct regular cybersecurity training sessions for all employees. Educate staff on recognizing phishing attempts, safe internet practices, and proper data handling. Create a culture of security awareness to reduce the risk of human error.
Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access. Use strong encryption standards and regularly update encryption keys. Ensure that only authorized users have access to decrypted data.
Network Security: Implement firewalls, intrusion detection systems, and secure network configurations. Use virtual private networks (VPNs) for remote access to protect data over public networks. Regularly monitor network traffic for unusual activity.
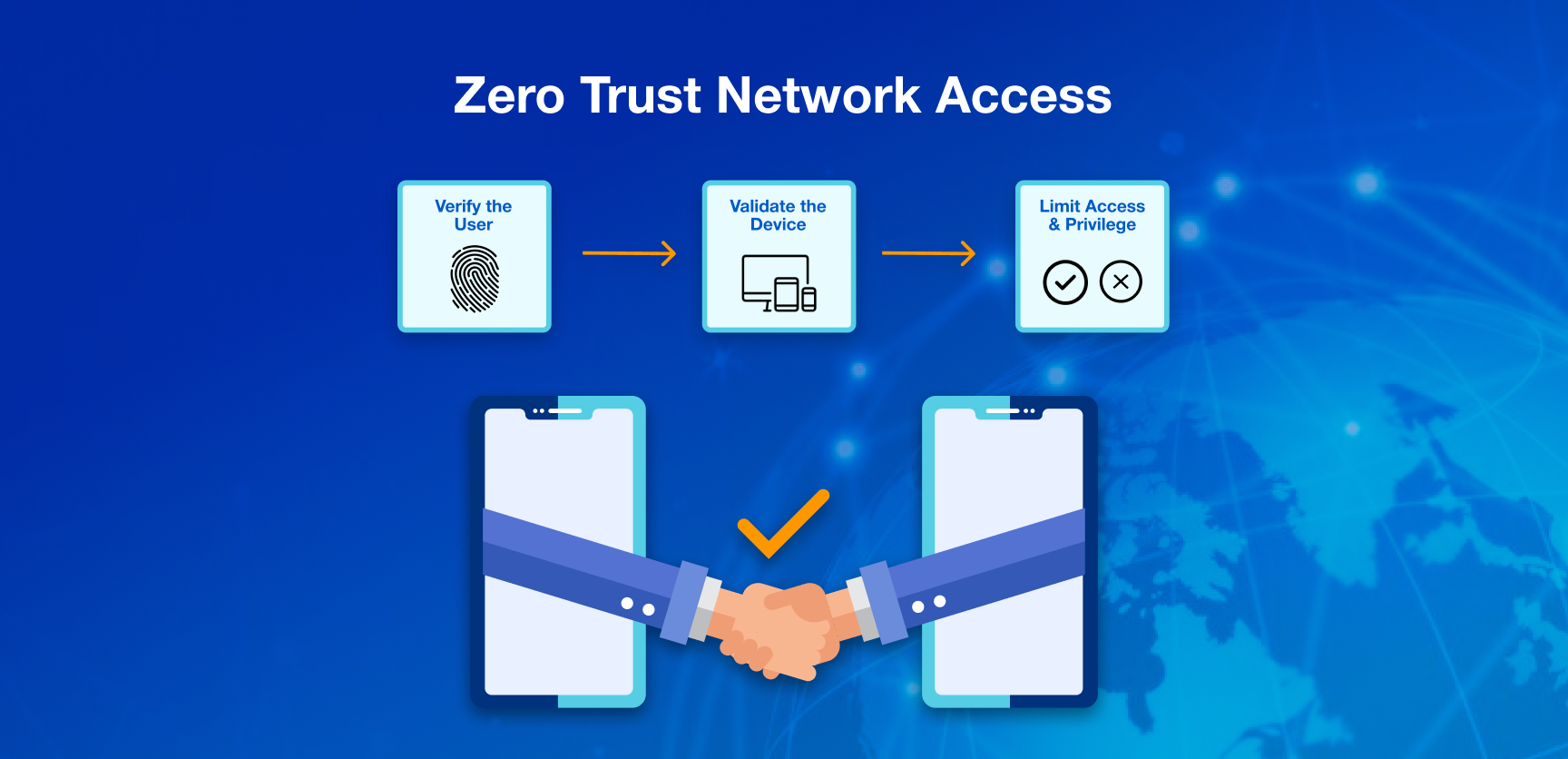
Zero Trust Network Access (ZTNA): Adopt a Zero Trust approach where no one is trusted by default, even if inside the network. Verify every user and device attempting to access resources before granting permission. Continuously monitor and assess security postures to maintain strong defenses.
Regular Security Audits and Vulnerability Assessments: Conduct regular audits to identify and address security weaknesses. Use vulnerability assessment tools to scan for potential threats and take corrective actions. Keep detailed records of audit findings and remediation efforts.
Backup and Disaster Recovery Plans: Regularly back up critical data to multiple secure locations. Test backup and recovery procedures to ensure data can be restored quickly in case of a breach. Develop a comprehensive disaster recovery plan to maintain business continuity.
Compliance with Data Protection Regulations: Stay informed about relevant data protection laws and regulations, such as GDPR or CCPA. Implement measures to ensure compliance, including regular audits and employee training. Keep documentation and evidence of compliance efforts to avoid legal penalties.
Future Trends in Data Breach Prevention
Artificial Intelligence (AI) and Machine Learning: AI and machine learning will play a bigger role in identifying and responding to cyber threats. These technologies can analyze vast amounts of data quickly, spotting unusual patterns and potential security breaches before they cause damage.
Quantum Encryption: As quantum computing advances, traditional encryption methods may become vulnerable. Quantum encryption offers a new level of security, using the principles of quantum mechanics to create virtually unbreakable encryption keys, ensuring data remains secure against future threats.
Biometric Security: Passwords and PINs may become a thing of the past as biometric security gains popularity. Using fingerprints, facial recognition, or even retina scans to authenticate users can significantly enhance security by making it much harder for unauthorized individuals to access sensitive information.
How PureDome Helps
PureDome helps protect your business from data breaches by providing advanced cybersecurity solutions. It offers strong encryption, multi-factor authentication, and robust network security to safeguard your sensitive information.
PureDome also supports Zero Trust Network Access (ZTNA), ensuring that every user and device is verified before accessing your network. With PureDome, you can stay secure and compliant with the latest data protection regulations, giving you peace of mind in an increasingly digital world.
Frequently Asked Questions
What is a data breach?
A data breach occurs when unauthorized individuals access confidential information without permission.
How can I prevent a data breach in my business?
Use strong passwords, multi-factor authentication, regular updates, employee training, encryption, network security, audits, backups, and comply with regulations.
What is Zero Trust Network Access (ZTNA)?
ZTNA is a security model where every user and device must be verified before accessing network resources.